In this blog, we talk about data breaches and data leaks a whole lot – we have explored the possibilities of Discord suffering a data breach a while back, we have told you how should you go about preventing data leaks, etc. In this blog, we will cover data leaks from a different point of view – we will tell you what they are in the first place. Let’s get started, shall we?
Data Leaks – What Are They?
Put simply, a data leak is an incident exposing sensitive data. To different people, sensitive data has different meanings, but for most, sensitive data is comprised of multiple data classes:
- Email addresses
- Usernames
- IP addresses
- Geographical locations
- Credit card details
- Other sensitive information.
If a data leak leaks only email addresses or usernames, it may not be very sensitive because there would be no associated passwords, locations, or credit card details – however, as you might have guessed, the more data classes are exposed, the more sensitive the data leak becomes.
Are Data Leaks Harmful?
Now that you know what a data leak is, a natural question might arise – are all data leaks harmful? And the answer is – everything depends on the nature of the data leak. Data leaks can be classified into three or four categories and they are:
- Low severity data leaks – such data leaks may contain usernames of users that once played on RuneScape private servers, some such data leaks may also contain IP addresses of users, but such data leaks don’t usually involve passwords.
- Neutral data leaks – with data leaks belonging to such a severity range, some harm can be done: think about the same example as with low severity data leaks: neutral severity data leaks may also involve passwords that would allow attackers to mount identity theft attacks.
- Moderate-severity data leaks – data leaks in such a severity range may leak usernames, email addresses, IP addresses, and unhashed passwords or passwords hashed with a weak hashing algorithm. The vast majority of data leaks in this day and age fall in this category.
- High-severity data leaks – such data leaks aren’t very frequent, and the most frequent victims of such data leaks are companies that deal with insurance records (think Experian and the like) or smaller banking firms.
Most data leaks fall within either the neutral or moderate severity range, however, no matter what range the data breach falls in, some damage can be done nonetheless: it might seem that data breaches falling within the low severity range aren’t very important for the attacker as they don’t contain much data, however, such thinking is usually wrong – most blackhat hackers collect data breaches, then use them as part of credential stuffing attacks. And credential stuffing attacks are where attackers are usually able to do the most damage – by reusing the usernames, emails, and passwords from an older data breach, they’re able to perform a data breach into another service.
Data Leaks vs. Data Breaches
Many people confuse data leaks with data breaches – a data breach occurs when a service gets broken into (i.e. hacked – a data breach is the result of a cyber attack), while a data leak often occurs unknowingly – say if an employee at a company X would have accidentally uploaded sensitive data to a server that is accessible by anyone, that’s a data leak.
That’s not to say that one type of attack is less dangerous than the other, though – far from it. Both data leaks and data breaches come with their own set of problems that are posed to security experts, developers, and decision-makers alike. The pain to the people involved is only one piece of the puzzle – after a data breach or a data leak is discovered, most of the work has to be performed by security engineers that then forward information to the decision-makers of the company (the board, the CEO, or both.) Data leaks are usually dealt with swiftly – companies usually go through these steps to plug the leaking hole:
- A data leak is discovered. More often than not, the company usually discovers that the data leak was performed by a current or former employee of the company.
- The source of the data leak is investigated, then the core problem is identified (e.g. was the data leak performed after a certain employee played with permissions too much? Was the data leak performed after someone loaded data into a publicly available cloud instance and forgot about it? Etc.)
- The problem is squashed – if the source of the problem is an employee, he or she is most likely required to undergo checks of his or her knowledge in the information security front by completing a couple of assessments, if not, security engineers plug the hole.
Data breaches, on the other hand, are usually approached a little differently: they’re usually not discovered until some incident occurs (think credential stuffing or the like) or after customers complain they cannot log in due to the fact that somebody has changed their passwords.
The first step in such a scenario is, of course, to forward information about the incident to the security engineers at the company or the CSO itself, and then decide whether we need to hire a data breach forensic team to investigate the incident, and if not, how should we deal with it ourselves, and then finally to reset all of the passwords belonging to all of the users.
Dealing with Data Leaks and Data Breaches
The best way to deal with both data leaks and data breaches happening both now and about to happen in the future is by educating ourselves on what happened in the past and using that knowledge to shape the future of a more secure web – and data breach search engines like BreachDirectory can help you do just that: not only will BreachDirectory provide you with a data breach search engine that is able to tell you what information of yours (an email, a username, an IP, or a domain) might be at risk of identity theft and allow you to swiftly change your passwords so you’re no longer at risk, but the BreachDirectory API will also provide an API capability to help you integrate data into your own company to assist your employees with OSINT-related tasks.
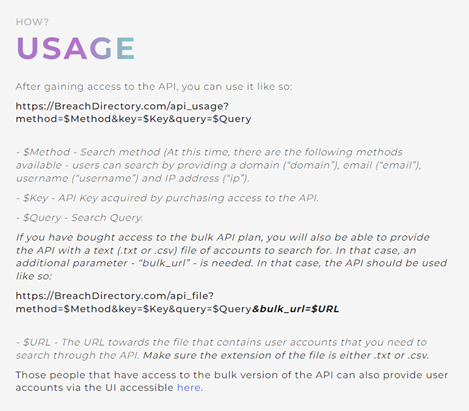
The API documentation will walk you through on how to use the API no matter what kind of plan you might be using – the API is a fit for all use cases from small single-user projects to larger enterprise appliances with its bulk API capability.
Here’s how the API documentation looks like:
Summary
Data leaks and data breaches are frequent sources of confusion – a data leak usually happens when someone discloses sensitive information that shouldn’t be disclosed on accident, while a data breach happens with a clear purpose to harm – in most cases, it’s the direct result of a cyberattack.
We can protect ourselves from both data leaks and data breaches by utilizing data breach search engines such as the one provided by BreachDirectory to protect ourselves, our loved ones, and our employees – we hope that you’ve enjoyed reading this blog, come back to the BreachDirectory blog to learn more in the future, and until next time!