A backdoor is a very frequent term in the circles of hackers. But just what exactly is it? What does it do and how does it appear? Is it harmful to the infrastructure of an application? That’s what we’re figuring out today.
What Is a Backdoor?
Once a hacker breaches a system (let’s call it “X” for the sake of simplicity), the hacker usually performs the following actions, one by one:
- The hacker logs in to the administration panel of the application.
- The hacker performs actions as he or she seems fit (the actions might include reading messages, etc. – depends on the application that is being breached.)
- The hacker leaves a backdoor so that he could come back to cause harm to the application in the future.
- The hacker takes a copy of the database and the data within it.
- The hacker cleans up after himself (removes all of the access logs, etc.)
- The hacker logs out.
Take a close look at the step #3 – the hackers usually leave a backdoor after performing certain malicious actions at their discretion – a backdoor usually refers to a piece of code that allows a hacker to regain access to a specific application even after the data breach has been contained. To leave a backdoor, hackers usually leave specific pieces of code, some of which are very simple and straightforward, others more complex, but all of them complete one mission – they provide a hacker with the ability to gain access to the application and cause havoc in the future.
Examples of Backdoors
You can see a couple of examples of backdoors below (all examples are based on the PHP programming language):
- There’s a piece of code that is perhaps the simplest backdoor ever – such a piece of code evaluates a command (GET parameter “cmd”) with the
system()command – essentially all commands put forth in the cmd parameter will be considered to be Linux commands, and provide output as such. Simple, but incredibly dangerous:<?php system($_GET[‘cmd’]); ?> - Backdoors can also look like so (this one evaluates a command in the parameter “cmd” and puts the result in between code brackets):
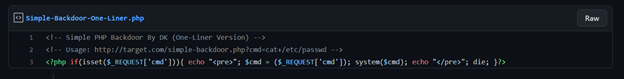
- Backdoors can be implemented into the code through git as well – for example, in 2021, hackers allegedly breached an internal git server of the website PHP.net (basically the PHP documentation) and backdoored the source code (source – ArsTechnica):
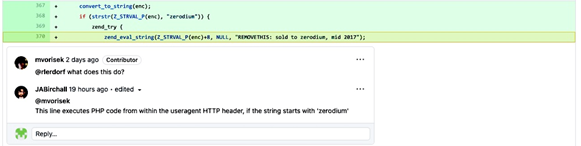
You get the point – backdoors are usually hidden in the code and they provide a way for the attacker to cause harm to our applications in the future. Once attackers regain access, the cycle repeats – they may even slip in one or two additional backdoors inside of the code as well!
How to Protect Your Applications?
Now that you know what backdoors are and what they can do to your web applications, you should also know how to protect your applications against such threats. Fortunately for us, developers, there are a couple of tools that help us do just that – one of such tools is called a PHP Shell Detector. The tool is apparently able to find and identify shells written in PHP, CGI (Perl), or ASP. The tool is released under the MIT license, and has over 600 known shell signatures in its database.
As far as other programming languages are concerned, we’re sure that they have similar offerings – search around for “shell detector”, “backdoor detector” and you will find something for sure.
A different way to remove backdoors would be to find and remove them manually, but for that you would need a little bit of knowledge around the security space as well as a list of malicious functions to detect. Here are a couple:
system()– returns the last line of a command specified in the brackets.shell_exec()– returns the output of a specified command.eval()– evaluates a string as if it would be code.passthru()– executes a system command and provides the output in a raw form.popen()– executes a specified command, creates a “pipe” between the application and the command, then provides a pointer to a stream of the pipe.proc_open()– same aspopen, but this command allows a script to work in conjunction with other scripts.pcntl_exec()– executes a specified program.
Also watch out for backticks that may be frequently specified as “\`\`” – such an approach would let an attacker execute a command in the same fashion as when using shell_exec().
Knowing the aforementioned commands will let your application continue riding the security highway – however, if you wish to protect your entire team and not only your application, you would need to employ different measures.
Protecting Your Team
By employing the search engine built by BreachDirectory and the BreachDirectory API in conjunction, not only will you be able to search whether you’re exposed in known data breaches and register for notifications should you be exposed in the future, but you will also be able to provide BreachDirectory with email addresses, usernames, IP addresses, or domains, and get a JSON response denoting whether they’re exposed or not in return. The JSON response will help you implement the data inside of the infrastructure of the company you work at to better protect your employees, contractors, and everyone else that might be close to you. Give the BreachDirectory API a try, and until next time!
