There’s no doubt about it – there are many web application security solutions from various companies. Each of them solve a different problem or work on the same problem, but in a different way than other security solutions do – most web applications work on the 7th (Application) layer of the OSI model (specified below):
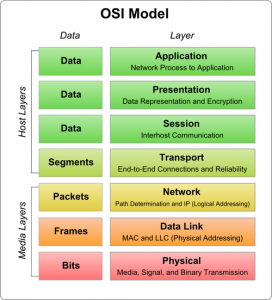
Since applications are ever-evolving, most web application security solutions available fall into one of the following categories:
- Testing – these are the tools or companies that provide penetration testing services. Think about penetration testing reports – the more thorough the report is, whether manual or automated, the better it is for the client because the client can better protect the infrastructure of their application.
- Monitoring – think about Intrusion Detection Systems (IDS) and the like. The companies that provide such software solutions help us secure our web applications from threats like SQL injection, Cross-Site Scripting, Cross-site Request Forgery, and the like. A big problem here is that the libraries backing such tools need to be frequently updated because attackers are constantly evolving, and with them, threats that need to be blocked do too.
- Prevention – the software solutions in the prevention category are mostly centered around the most popular ways cyber criminals operate and help us prevent becoming a part of the cyber-crime statistic.
- Education and Self-Protection – the software solutions in this space help companies and developers alike to educate their employees, contractors, and clients on cyber security matters; services falling in this category include data breach search engines and API solutions like the one provided by BreachDirectory, security tooling based around education on security matters on the web, etc.
Differences in Problems Solved by Web Application Security Solutions
As already mentioned, web application security solutions usually fall in one of the aforementioned categories and the problems solved by them directly depend on the category they fall into. However, as there many problems in the web application security space, there are many differences in the ways they are solved as well, and those differences pose their own unique problems to the companies themselves. For example, password managers like 1Password, LastPass, and others solve a huge problem of password security – these password managers generate secure passwords and store them locally in encrypted vaults that can only be decrypted with keys that are generated once the „main“ – „master“ – password is entered into the software solution. Essentially, people have to remember one password to unlock access to all of their other generated passwords stored in the password vault.
One of the primary questions centered around password managers, though, is whether securing all passwords and secrets with one password (hence the name – LastPass, 1Password, etc.) is secure and password managers always have that in mind – all of them are built in such a way that anticipates all possible attacks; they are not capable of granting access to data (passwords, secure notes, credit cards, etc.) that they don‘t have access to themselves.
Some security solutions centered around the cloud (think Web Application Firewalls as a Service and similar solutions) face even more complex security issues – they do not only have to comply with GDPR and other security regulations but also need to make sure that the attack vectors they block do not cause more harm than good, e.g. firewalls should not block basic inputs deemed as a necessity for their client websites to operate but at the same time, they should be capable of blocking basic threats to security like SQL injection, XSS, CSRF, and DDoS attacks.
Companies providing security consulting services face different types of threats – some of them might be attacked by the attackers they‘re defending against, and some of them might fall prey to phishing attacks (according to various sources, between 2013 and 2015, both Facebook and Google lost more than $100 million USD due to complex phishing campaigns), some of them might even receive calls from attackers, some of their employees might receive threats in the form of „you either stop working there and investigating crimes, or we act appropriately“, etc.
For some employees working at these kinds of companies, threats are an unfortunate reality as well because the more threats their companies defend applications against, the more likely attackers are to go after them. However, the security community is big and it only gets bigger over time – the bigger the security community is, the less likely nefarious parties are to threaten or go after a researcher.
Summary
There are various companies offering security solutions for the web – each of them fall into a separate category that solves various threats appropriate to itself; however, each of them has something in common – they all protect us from threats and nefarious parties, sometimes at the expense of putting themselves at risk as well. We hope that you‘ve enjoyed reading this article and that you‘ll consider searching yourself up on BreachDirectory and using its services to ensure you‘re not exposed to threats to your identity, and we‘ll see you in the next one!
