If you’re reading this blog post, chances are that you’ve read the message “this password has appeared in a data leak” when using some sort of data breach search engine. Most ethical data breach search engines like the one provided by BreachDirectory do not provide passwords when searching for a specific account (to know the exact reasons why, please refer to our earlier blog post regarding the ethics of data breach search engines), but if you’ve been fortunate (or unfortunate) enough to read such a message, this blog post should help guide you in the right direction.
What Does This Mean?
If you’ve been informed that your identity (your account’s username, password, or any other affiliated details) have been compromised, that’s never good news. First off, that means that the details of your account have appeared in a data leak. Secondly, that probably means that some of your account details are now in the hands of some nefarious party that keeps thinking about how to exploit them to get the best possible benefit (benefit for the attacker, obviously.)
What Should You Do?
Once you have gotten ahold of such a message, you should immediately change the password of the account in question in the service that was affected. For example, if you’ve searched for your account on a data breach search engine like the one provided by BreachDirectory and the search engine came back with a message like so:
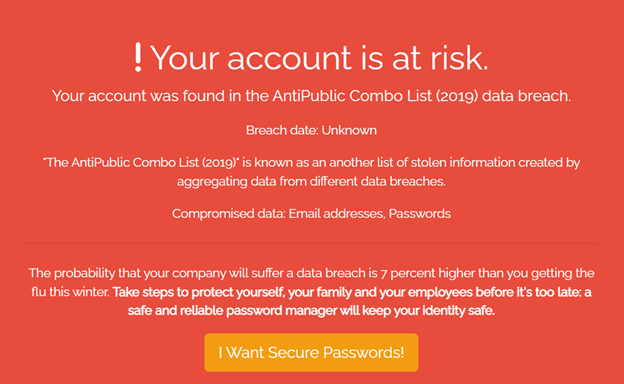
That means that your account (in this case, its associated email address and password) has been exposed in a data breach called “AntiPublic Combo List (2019.)” The “combo list” addition means that your account has probably been used as part of a credential-stuffing operation against some other systems where attackers aim to log in to services by simply trying out all possible email address and password combinations from data leaks that have occurred in the past.
In this case, stolen data from the leaked data breach only included email addresses and passwords, so you should reset all of the passwords in all services associated with the email address in question. If you see that there’s more data that has been exposed or the stolen data in the leaked data breach included not only email addresses and passwords but also geolocation data, names, surnames, and credit or debit card numbers, you should not only change the password associated with all related accounts but also inform your bank of possible fraudulent operations and possibly get in touch with the police too.
Tl;dr: once you have gotten ahold of such a message, act in accordance with the data that has been breached. For less sensitive cases (like the leakage of email addresses, usernames, and passwords), simply changing your password and enabling two-factor authentication on all of your accounts will probably be enough, however, for more severe cases, you should consider taking other actions as outlined above.
The Importance and Ethics of Data Breach Search Engines
You wouldn’t have known that your email address, username, or password has appeared in a data breach unless you’ve used a data breach scanner like the one provided by BreachDirectory. Not all data breach search engines are made equal, though – just like we’ve explained previously, a data breach search engine can be of more use to an attacker than you (if it displays any kind of data related to your account, that’s a huge red flag and you should stop using it immediately – refer to our earlier blog post to learn why), but if you’re confident that the operators behind the search engine operate on the ethical side (i.e. if you see that the search engine only provides a message of the account being at risk or not and doesn’t provide any additional information that could be used to harm you), that’s okay.
The same with API services – if an API service provided by the data breach search engine provides access to passwords or other data that is deemed to be too sensitive, that’s a problem. Sure, a good data breach API will allow you to know what your password was at least in a hashed form, and from one side, that’s a very good thing – however, a terrible thing from another (it will most likely be used by attackers to mount identity theft attacks.)
The bottom line is this: when using any kind of a data breach search engine, you can never be sure of the intents of its operators. Data breach search engines operating on the ethical side will never let you see the entirety of your data in respect to privacy – instead, they will alert you whether your account has been exposed to a data breach or not.
Summary
Once you have seen one or more messages similar to “your account has appeared in a data breach”, “this password has been found in a data leak”, you know you’re in trouble. However, don’t fret – in many cases, such a message means that you’ve successfully made use of the benefits provided by data breach search engines or their API counterparts. If you’re certain that the data breach search engine you’ve just used is built in an ethical fashion (i.e. it doesn’t provide any information that would help an attacker), just change your password associated with the email address or username you’ve just searched for, and in many cases, you will be good to go. If you see that the search engine provides some more information such as passwords, IP addresses, geolocation data, etc., be aware that there’s a good probability that such a data breach search engine is operating on the darker side.
However, whatever’s the case – once you have seen a message similar to “this password appears in a data leak”, act in accordance with what data types have been leaked (we’ll have a blog post centered around that soon), and you should be good to go. Best of luck – the internet is a strange place and it’s a place full of crooks, so make sure to be safe out there! Try to not get lost in the data breach jungle, and until next time.
