Choosing a security question is something almost all of us have to do when registering to use a service on the web. Doesn’t matter if the service is an email provider, a gaming platform, or a social media website – an answer to a properly chosen security question could be a matter of life and death if an attacker has our password at hand.
So, how exactly do you choose a proper security question to protect your online accounts? This is what we’re looking into today.
Why Do You Need a Security Question?
First things first – why do you need a security question in the first place? In most cases, the answer is simple and straightforward – to prove your identity to the service you wish to use. You see, after the service you use senses a login from a different location or a successful login after many unsuccessful login attempts, it flags your account as “suspicious” and in order to remove the flag and use the account as intended, you must correctly answer the security question you have set up when registering to use the service.
How to Choose a Security Question?
Now towards the most important question – how to choose a safe security question?
The answer to this question is simple but complex at the same time: choose a question that makes no sense, but the one you can remember. The best way to do that is by using a password manager – password managers like the ones provided by 1Password, LastPass, or Dashlane serve the vital purpose of protecting all of our passwords behind a single master password and storing an encrypted vault of our data locally on our computers so that no-one could access it, and most of them have a couple of additional features including secure notes.
Secure notes are the perfect venues to store security questions and answers to them because they are stored securely:
- All password managers encrypt information with AES-256 and store it in a locally encrypted vault – most of the password managers available for us to use also let people familiarize themselves with the security model they’re based upon.)
- All of the data is stored in a location that will always be accessible to us (all of the most popular password managers can always be accessed via phone, tablet, or PC, and they are all available offline as well.)
If the service you’re using lets you create the security question yourself (most don’t), create the security question in such a manner that it doesn’t make the answer obvious to begin with. Aim to create the security question centered around things you don’t like to do or answer the question in such a way as to throw potential attackers off the rails. The aim of this is to disorient an attacker that knows a little about your biography (it’s not unusual for attackers to dox their targets before accessing their online accounts) – a nonsense answer is perfect, while a personal question with a truthful answer may be the key to compromise.
For example, a security question like “What’s Your Favourite NBA Player?” with a truthful answer of “Lebron James” would be insecure, but an answer like “legume pawnshop pike” (generated with a password manager – see below) or even a false name and surname like “Jack Candyfloss” would do the trick.
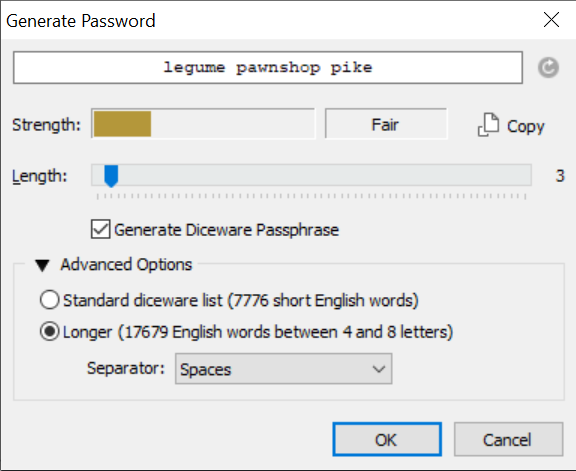
The key to choosing a safe security question is two-fold:
- The security question should not be tied back to you as a person in any way – attackers are likely to investigate your background and biography. For short – your answer ideally should be a lie.
- The security question should ideally be cryptic if you’re using a password manager or consist of a rememberable passphrase if you’re not.
Follow these two steps outlined above, and you should be good to go. Now, even if an identity thief knows your password, he will be faced with a security question – the question to which only you will know the answer to.
However, proper answers to security questions are only one piece of the puzzle – to stay safe on the web and offline, make sure to choose secure passwords for your online accounts, search for your accounts on the BreachDirectory data breach search engine and take decisive action if the data breach search engine determines they’re at risk, and consider implementing the BreachDirectory API into your infrastructure to secure the team working at your company. We hope that this blog post has been informational – share it with your friends and colleagues, and until next time!
