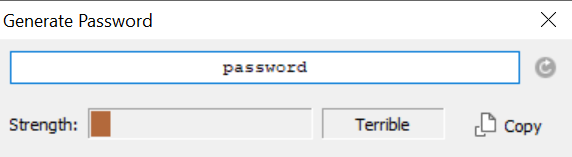
Password strength checkers are nothing new – they’ve been around for quite a while and their core purpose is to evaluate the strength of a given password. Here’s what one of the most popular password managers – 1Password – think of the word “password” as your password:
And here’s what a secure password looks like:
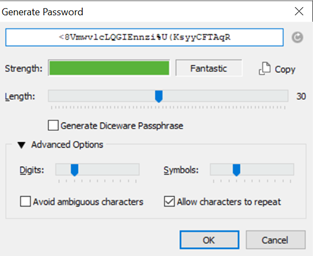
As you can see, both of the passwords that were provided to 1Password had a password strength meter – just that one password was terrible, the other fantastic. The strength of a given password directly depends on its entropy: in simple terms, that’s a measurement of just how unpredictable a given password is. The more unpredictable a password is, the better it’s strength.
Password Managers and Password Strength Meters
Of course, passwords like the one seen above are close to impossible to remember, and that’s why they’re generated using a password manager – password managers are software solutions that not only help us generate secure passwords like the one shown above but also store them securely: all of our passwords can be accessed with a single so-called “master” password – the master password unlocks access to our password vault (the vault where all of our secrets are stored.) Learn more about the security model of password managers here.
Coming back to password strength meters, though – not all of them are built equal. The strength measurement, message, and entropy calculation heavily depend on the developer of the password strength meter, and that’s why it’s crucial to select reliable service providers – when thinking about whether to trust a password strength meter or not, consider the following questions:
- Who developed the password strength meter? A reputable company or some randy in a garage?
- What the password strength meter is developed for (i.e. what is its use case?) – is the password strength meter supposed to be used as a standalone software solution, or is it supporting a plugin, a registration process, or something else?
- Who is using the password strength meter? Are any reputable companies using the password strength meter or is it built with a general-purpose use case in mind? Reputable companies using the tool usually signal reliability, however, no-name bloggers using the tool might not.
The aforementioned questions will help you evaluate the password strength meter. Most people avoid getting caught in the details, though – and that’s a good thing. Enter a password, enter it again to confirm it, then simply look for the green bar to appear within the password strength meter if it’s present (if the bar is red or orange-looking most software solutions won’t even let you register), and you’re good to go!
Most password strength meters operate in the following way:
- They check whether you’re pressing a key.
- They check what kind of key are you pressing (is it uppercase, lowercase, is it a number or a character, etc.)
- They classify the strength according to multiple parameters at the same time:
- They check how many characters are in a given password.
- They check what characters the password consists of.
- They classify the password as “weak”, “acceptable”, or “strong” (other classifications may exist depending on the password strength meter.)
- They provide the strength meter to you in color – red means that your password is terrible, orange most likely means that your password is weak, a green-ish bar means that your password is acceptable, and a green bar means that your password is very strong. Woohoo!
That’s it! The work behind the scenes of password strength meters is not exactly rocket science – is it?
Passing the Password Strength Meter Test
Once you see that a password strength meter is in place on a webpage, you must pass it – there’s no other way through (otherwise the website will either respond with a warning or error out as a whole) – here’s what you can do for the best chances to pass:
- Make sure your password contains both uppercase and lowercase characters, as well as numbers and symbols.
- Make sure your password is at least 8 characters long (aim for 16 and above for the best results.)
For the best results, don’t reuse a password you’ve used anywhere else (reused passwords are one of the primary reasons credential stuffing and identity theft attacks are so successful), and consider using a password manager too – you may want to read up and familiarize yourself with their security architecture and evaluate all of your possible options before using them though.
Staying Safe From Identity Theft
While password strength meters will take you far, they won’t exactly protect you from identity theft and your company – from data breaches. That’s the job of data breach search engines – the data breach search engine provided by BreachDirectory is not only able to inform you if your account has been exposed in a data breach that has happened in the past and notify you if your account appears in a data breach in the future, but it also comes with a data breach API querying capability letting you secure everyone within your company and team as well – provide the BreachDirectory API with a domain, username, email or IP address and the API will come back to you with a response that will let you identify what kind of data of yours is at risk of identity theft. The data breach search engine, on the other hand, will tell you what account of yours and as a result of what data breach could’ve fallen in the hands of hackers.
Make sure to give it a try today!
Summary
Password strength meters aren’t news to anybody – they’ve been around for a really long time, and we can confidently say that they’re here to stay at least for a while.
Not all password strength meters are made the same, but for the most part, they measure the entropy of passwords given to them – the stronger a password is (the more special characters, numbers, and letters it contains), the higher its entropy is and the greener the status bar will become. Aim to see a completely green password strength bar when using any password strength meter and you will be on the safe side – doing so might become a little difficult without a password manager like 1Password though, so consider using those and employing the features of data breach search engines and their API counterparts at the same time, and you should be good to go. Until next time!
