Data breaches have one thing in common – they affect a myriad of online users and various data classes of data as well. One of the main data classes that are affected are email addresses – what can cybercriminals do with them? That’s what we answer in this blog.
Data breaches are notorious for the data breach classes that are being stolen. Each data breach affects varying classes of information ranging from usernames, email addresses, and passwords to geographical locations, full names, and credit card details. Many attackers collect stolen data to achieve various purposes – some use the data for credential-stuffing attacks, some use the data to stalk people, some use the data to accomplish identity theft attacks, and attack various services that are of interest to them.
Email Addresses
One thing almost all data breaches have in common, though, are email addresses – as far as data breaches are concerned, email addresses in them are frequently associated with usernames, IP addresses, and other miscellaneous information. Email addresses, though, are amongst the most frequently stolen pieces of data and it’s very easy to understand why – almost all services store email addresses in their database because email addresses are one of the most frequently used assets to log in to a service.
Once email addresses are stolen from a database, they’re usually stolen together with hashed or plain text passwords. In a data breach, stolen data classes (emails included) usually look like so (in this case, the password is hashed with MD5):
[email protected]:fe01ce2a7fbac8fafaed7c982a04e229
Or like so (in this case, username is the username):
[email protected]:username:demo
The data looks like this mostly because it’s exported from a MySQL-based database using the SELECT * INTO OUTFILE query: cybercriminals love this approach since it’s quick, allows them to dump data out of the database in a quick fashion, and the text file usually occupies less space on the disk than output provided by mysqldump or other tools.
Many cyber criminals use such data for credential stuffing – an attack where data stolen from one service is used to access another service and steal data from that service too. Email addresses alone are valuable too – since many attackers collect data over the period of months or even years, if they have a “target” (a person that they’re targeting), re-used data is a gold mine since the data taken as a result of the data breach into the service B might reveal more data than the data stolen from the service A.
As such, attackers are easily able to map out various kinds of information about a person including, but not limited to:
- His or her email address and, if applicable, a list of the most frequently used usernames by that person
- A set of passwords that are most frequently used by that person
- His or her approximate location by looking up the IP address
- His or her phone number
- If applicable, a list of aliases (people) who that person may know by deriving data from other data breaches, etc.
With that information, attackers can do some damage ranging from utilizing the data to mount identity theft attacks to making unsolicited orders of pizza to that address, they can call the number and start harassing the person, etc.
Data Breach Search Engines
Data breach search engines are known to collect data as well – and different kinds of data breach search engines collect various pieces of data as well! The operators of such data breach search engines usually don’t choose data to include or exclude (i.e. they collect all of the possible data leaks), however, many data breach search engines fall into either the ethical or unethical categories.
Ethical data breach search engines such as the one provided by BreachDirectory offer both a data breach search engine and API functionality to help keep companies, individuals, and universities in their OSINT endeavors – such data breach search engines don’t display unnecessary data that can be used to cause harm (e.g. passwords, credit cards, etc.) and only let people search for their data (usernames, email addresses, IP addresses, or domains) by informing them whether their account is at risk or not, and their API doesn’t display any sensitive data (passwords or other details) as well, while unethical data breach search engines act in a destructive manner that brings thousands of dollars of profit to their operators and massive damage to those impacted. Consider this: you visit a data breach scanner, search for an email address, and upon getting a couple “hits” (meaning that the account exists in the database of the data breach search engine) the data breach checker provides you with the username of that user, IP address, phone number, an associated password, and other related information? That wouldn’t be fun, would it?
Yeah, we think so too. That’s why BreachDirectory was built in an ethical manner – we never display sensitive data neither to those using the data breach scanner, neither to those using their BreachDirectory API key.
BreachDirectory also has a couple of plans applicable to all manner of use cases – from simple use cases where the API is being queried a couple hundred times a month, from more complex use cases like reselling the API or querying the data breach search engine via the API in a bulk manner.
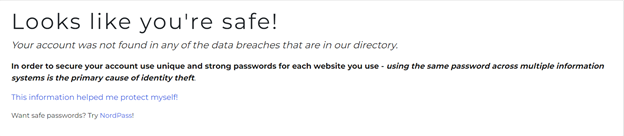
The output of the data breach search engine usually looks like so if you’re not at risk, while the outcome is a little different if the account is at risk:
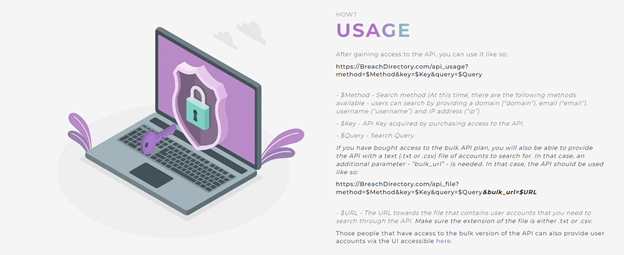
The API documentation is a little more complex, but at the end of the day it isn’t the end of the world either – it’s built to be understandable to pretty much anyone:
Summary
An email address is an extremely valuable piece of data to any attacker – since many emails also come with affiliated usernames and passwords, these pieces of data are very frequently used to mount identity theft and credential stuffing attacks if the password of the email is found in another data breach.
Data breach checkers (data breach search engines) are usually able to solve this problem, however, they’re also a very two-sided sword: some data breach scanners like BreachDirectory are built in an ethical manner, but many are not and the data derived from such data breach search engines are used to further mount identity theft attacks – that’s why many attackers are paying for them! Anyway, we hope that this blog has taught you something new – be careful out there, make sure you’re not at risk by searching yourself on our data breach search engine, and until next time!
