“Xmas came early this year. I present you a new rockyou2024 password list with over 9.9 billion passwords!” – said a hacker called ObamaCare. He’d referred to a RockYou.txt combo list – one of the biggest password compilations ever.
Preface
This is what the users of a popular hacking forum could’ve seen today:
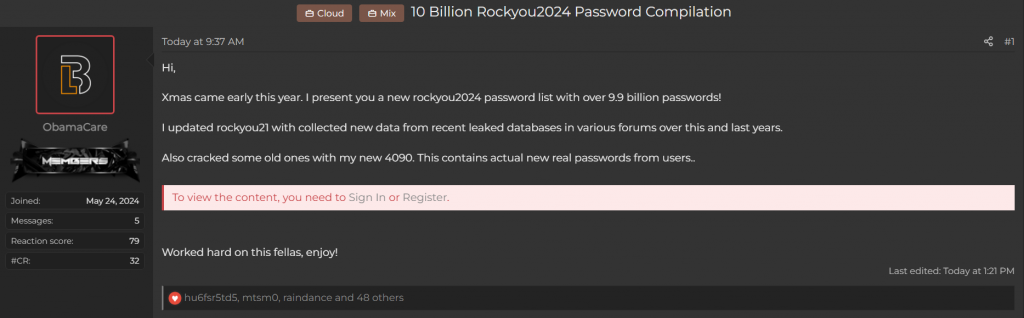
A hacker going by an alias of „ObamaCare“ has leaked one of the biggest password compilations ever – a password compilation containing almost 10 billion passwords! The anonymous individual also says that he‘d „cracked some old [passwords] with my new 4040“ and says that the list contains new real passwords from users, so you may want to change your passwords…
What is RockYou.txt?
RockYou.txt is nothing new to the security world – the RockYou.txt file refers to a big wordlist that was created after cyber attackers leaked over 32 million user details pertaining to the company „RockYou“ on the web. RockYou was a company that was formed in 2005 and dissolved in 2019 – the company was known for developing widgets for MySpace and doing other things, but since 2014, it has focused on acquiring rights to old-school video games.
Anyway, back to the RockYou breach – the RockYou.txt file wasn‘t shared in one part – according to SevenLayers, the wordlist fit for Kali Linux contained approximately 14 million passwords and was 134MB in size. It is said that the breach occurred somewhere in December 2009 – the breach is known as „RockYou.txt“ referring to a huge list of unencrypted passwords. Back in the day, many think that attackers breached RockYou by abusing an old SQL injection vulnerability.
In 2019, RockYou was dissolved, but since in the hacking community „RockYou.txt“ is known as a password list and not as the company that got dissolved, the hacking community quickly adopted the RockYou title to signify massive password breaches, such as the one today.
With that being said, it should be crystal clear that the RockYou.txt file is a massive compilation of plain-text passwords likely derived from past breaches. Many of our readers will also be aware that a file of a similar nature – the so-called „RockYou2021 list“ was also shared on the interwebs in 2021.
The 2024 edition of RockYou.txt seems to be formed by combining the passwords of massive data breaches (perhaps those that have occurred in 2024 or in 2023) and the most recent edition of RockYou.txt may contain passwords from the victims of hundreds or even thousands of data breaches that have occurred in the past.
What‘s the Problem with RockYou.txt?
RockYou.txt may seem like an ordinary password dump – after all, there are thousands of such password dumps being shared on the web these days, right? Well, there are, but they‘re not that big!
You see, the problem with huge password dumps like RockYou.txt is that attackers may use them to launch credential-stuffing attacks targeting innocent people – those people may work at government agencies, hospitals, schools, or other institutions, and, of course, the applications of companies – no matter how large or small they are – aren‘t protected from this behavior either.
The smartest decision you can make now is to update all of your passwords, and if you run a company or have built an app that‘s used by some people, make sure to implement adequate brute-force defenses – these will prevent possible credential stuffing attacks thus containing the possible fallout of RockYou.txt.
How to Protect Your Data?
With all the worrying news that you‘re presented with every single day, a natural question may cross your mind: „How do I protect myself from all possible attacks?“ Thankfully, protecting yourself is rather simple: all you need to do is follow the latest cybersecurity news and advice and make use of data breach search engines such as the one provided by BreachDirectory: data breach search engines are the appliances that will help you contain the fallout of RockYou.txt or any similar data breach compilations.
Data breach search engines such as the one provided by BreachDirectory work in a rather simple way and are frequently used for assistance in OSINT-based investigations by leading institutions, known software companies, and law enforcement. The data breach search engine provided by BreachDirectory looks like so:
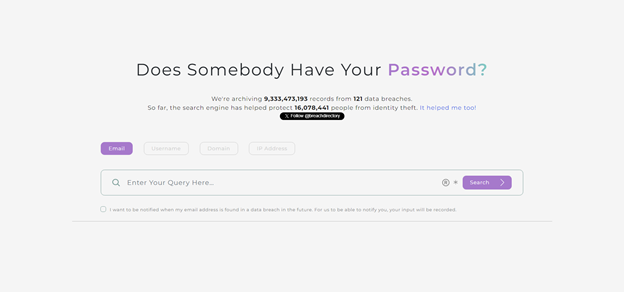
Data breach search engines let you provide your email address, username, domain, or IP address and tell you whether your data is found in any data breach:
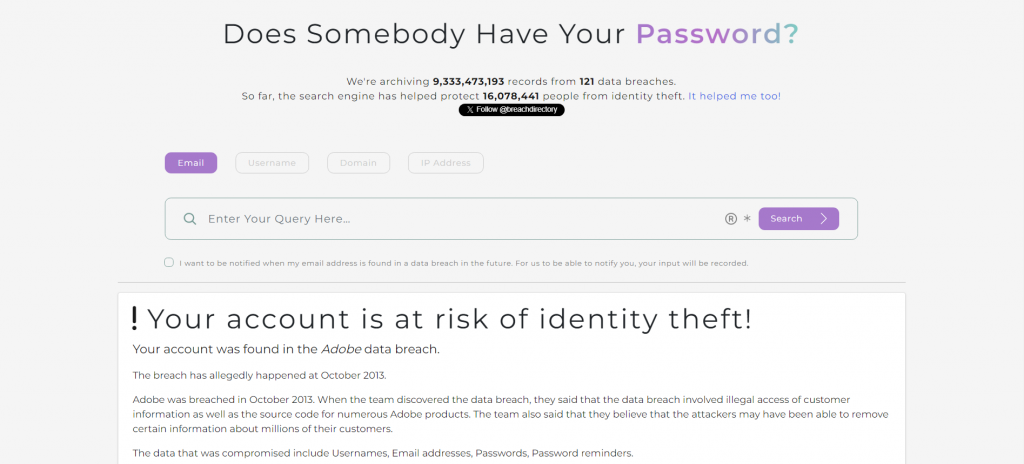
Most data breach search engines also have an API functionality – the BreachDirectory API can be used for single accounts or to scan through a set of accounts in bulk thus helping you protect a wide set of accounts at once.
With such data breach search engines at the helm, no password compilation should worry you, and credential-stuffing attacks derived from RockYou.txt or other mediums should quickly become a thing of the past.
Try the BreachDirectory API today – you won’t be disappointed.
Summary
The RockYou.txt list of 2024 is a password list (often referred to as a wordlist) that’s likely been derived from hundreds or even thousands of data breaches that have occurred throughout 2023 and 2024. The good news is that you’re armed to the teeth – by making use of data breach search engines like BreachDirectory and employing their API in your infrastructure or company, you can quickly make data breaches and password compilations like RockYou.txt a thing of the past.
FAQs – RockYou.txt
What is RockYou.txt?
RockYou.txt is a wordlist that was most likely made after a combination of hundreds or thousands of data breaches that have occurred in the past. Such wordlists frequently facilitate credential stuffing and similar cyberattacks.
How to Protect From Credential Stuffing Attacks Deriving From RockYou.txt?
The first fortress of defense against Credential Stuffing Attacks posed by wordlists like RockYou.txt is to use a reputable data breach search engine like BreachDirectory or its API appliances. Combine those two appliances and you will be equipped with powerful tools to help you fend off cyber attacks like never before.
How to Protect My Application From Credential Stuffing?
To protect your application from credential stuffing, you may want to look into rate-limiters, automatic log-off capabilities, denying logins from an unknown location based on an IP address, and of course, use strong passwords after using data breach search engines to find out whether you’re at risk of identity theft.