How to prevent SQL injection? Learn with BreachDirectory.com!
Preface
According to the OWASP Top 10, SQL injection is one of the primary ways attackers breach applications. Injection is a threat to note – and it will likely remain a formidable threat for those building applications in the near future. It is a formidable threat because of three key concepts:
- It is easy to write code that would be susceptible to SQL injection. Think about it – how often do we hear “Don’t provide user input straight into a query?” Too often, right? Yet, we still hear about SQL injection attacks. Developers can listen and follow directions – yet, seeing as injection attacks are still in the spotlight, it wouldn’t be far-fetched to say that they seemingly forget the basics far too often. With all of the responsibilities they have, it’s not a surprise.
- Injection attacks are easy to mount. That’s right – one of the reasons why SQL injection is a problem is because injection attacks are very easy to mount! SQL injection attacks can be mounted manually (a simple quote will often return a SQL syntax error) or be automated with tools like SQLMap or others. A couple of clicks and your database is toast. Cool, right?
- The risk/reward ratio of SQL injection attacks is very acceptable for an attacker. Lastly, SQL injection attacks are a problem because of the risk/reward ratio for a potential attacker.
These three concepts empower SQL injection and a piece of code susceptible to SQL injection looks like so:
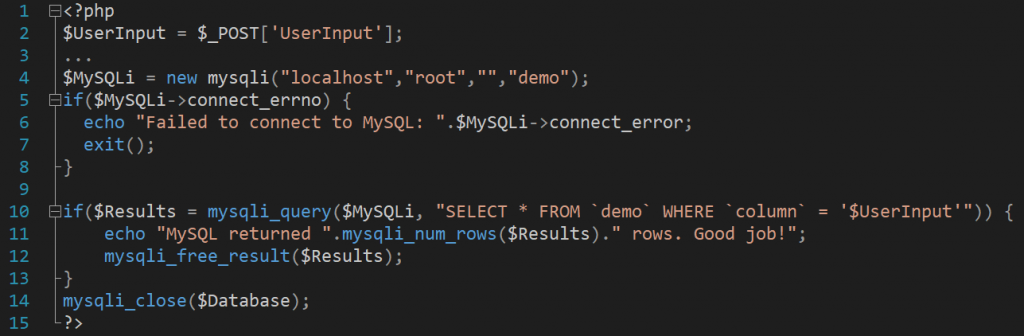
The above piece of code is susceptible to SQL injection because we provide user input straight into an SQL query. If that user input would be manipulated in such a way that makes it do something else than select data from our database, our data would be toast.
Say our input is as follows:
'; DROP TABLE `demo`;/*
Then, our database interprets it as follows:
‘;stops the current query from executing.DROP TABLE `demo`;drops the table under the name demo./*would turn everything after the;statement into a comment.
You can also use--with the difference being that/*can be used to comment on multiple lines, while--would only be applicable to one line.
The same SQL query in an SQL client will help you visualize the concept:
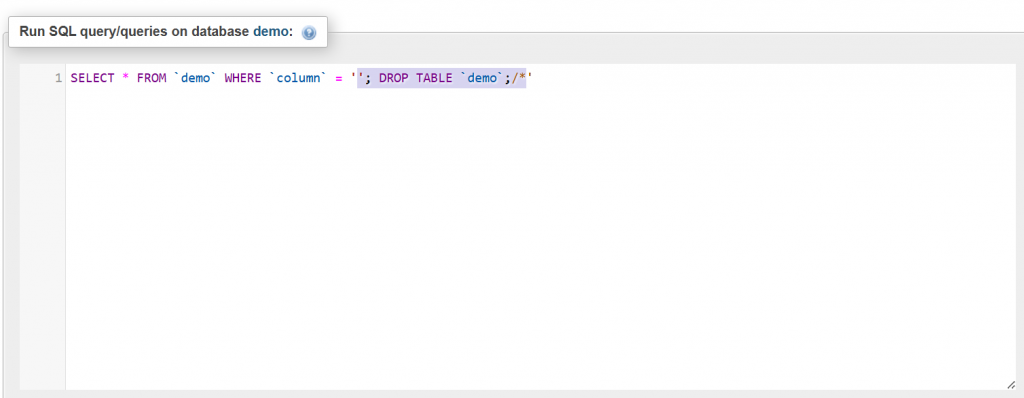
As a result, the demo table would be dropped (deleted.)
It gets even scarier – if the data inside of our tables can be dropped, it can also be modified or deleted, right?
How to Prevent SQL Injection?
Now, towards a way how to prevent SQL injection. Contrary to a popular belief, preventing injection attacks is quite easy – all we need to do is to avoid presenting user input straight into a SQL query. In other words, to prevent SQL injection, don’t provide user input into an SQL query. It’s as easy as it sounds.
Take a look at this example:
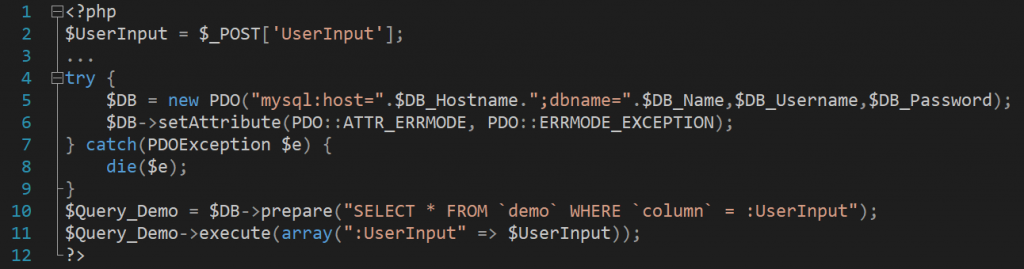
In the example above, we’ve mitigated an SQL injection attack by separating user input from the database query. That’s all you need to do!
Other Things to Note
Now that you have an answer to the question how to prevent sql injection, you should also consider other things too. Some of those things will inevitably concern the things you should consider if your application has already been attacked or if you are under any suspicion that it has. Follow the security guidelines outlined by OWASP – OWASP will tell you what attacks concern your application the most as well as walk you through the ways to prevent them.
Make use of data breach search engines too – data breach search engines like the one available at BreachDirectory.com will tell you what data of yours has been stolen and where, as well as advise you on what to do to further your security on the web.
Furthermore, consider reading books like Hacking MySQL: Breaking, Optimizing, and Securing MySQL for Your Use Case to better understand what makes your SQL queries break, how to optimize your database infrastructure, as well as how to secure it from data breaches coming your way.
Hope you’ve enjoyed reading this blog and until next time.
FAQ
How to Prevent SQL Injection?
To prevent SQL injection, don’t provide unfiltered user input into SQL queries. Prepared statements can help you do that and put your mind at ease.
What Other Attacks Should I Be Aware Of?
Aside from ways how to prevent SQL injection, also be mindful of other attacks in the OWASP Top 10 list. Such attacks include, but are not limited to Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), Open Redirect attack vectors, and others.
Finally, to further the security of your application, consider reading books like Hacking MySQL: Breaking, Optimizing, and Securing MySQL for Your Use Case to better understand what makes your SQL queries break, how to optimize your database infrastructure, as well as how to secure it from data breaches coming your way.