Your database is the backbone of everything existing in your application — this blog will provide you with ten database security best practices you can use to protect any database management system.
Preface
Your database is the backbone of your application — an application that acts as a cooking guide, software to manage invoices, cocktail making and delivery app, or perhaps a content management system for a forum. As such, it has to be protected adequately — and with the rise of data breaches during recent years and months, database security has never been more important.
Database Security Tips
We’ll get straight to the point — what are the points of advice you can employ to strengthen your database security? We have 10 of them — if there’s a need, we’ll dive deeper into those database security tips later on:
- Backup the data in your database: backups are an essential part of the security of any database management system, be it MySQL, MongoDB, TimescaleDB, or other DBMS. Database management systems have multiple ways to back up data: there are full backups, incremental backups, and differential backups. Backups can also either back up SQL statements that re-create the data (we call those logical backups) or back up files and act as physical backups instead. Different database management systems offer different software appliances to take copies of your data — we have
mysqldumpfor MySQL and MariaDB, Percona XtraBackup for data in Percona Server,pg_dumpfor PostgreSQL, SQL Backup Master for SQL Server, and other backup appliances for other database management system. - Encrypt the data within your database: aside from backups, keeping the data inside of your database safe at all times is an essential task to any developer or database administrator — make sure to follow database security and application security best practices when encrypting data inside of your database and follow all of the applicable privacy regulations, too. Hash passwords with BCrypt or Blowfish instead of MD5, censor some data within email addresses before displaying them if necessary, and so on.
- Make sure that all users within your database use strong passwords: to further strengthen your database security, ensure that all users within your database use strong passwords. Your database management system may as well come with plugins that enforce password security by letting you set the minimum length of characters, etc.
- Employ access control measures: all database management systems come with users. Those users have privileges that can be used as a measure of access control for users within your database and application. Avoid granting unnecessary privileges to users within your database — follow the “least privilege” principle: to strengthen database security, only grant privileges that are necessary.
- Enforce connection security best practices: database management systems also allow their users to connect to them using SSH or through SSL. Explore the possibilities offered by your specific database of choice and follow database security best practices in this realm, too.
- Use database firewalls: MySQL and other database management systems have appliances like the MySQL Enterprise Firewall — for MySQL, the MySQL Enterprise Firewall is a premium database security appliance that will set you back a couple thousand dollars should you decide to use it, but there are other, free, tools that you can make use in MySQL and beyond.
- Take physical database security into account: make sure your database server is located in a secure location, that the location is waterproof, and take into account natural disasters too. Hackers won’t have to do much work if mother nature owns your database to begin with.
- Make use of proxy servers and database load balancers: this one isn’t specifically a database security tip, but rather, a tip that may help you improve your database performance. Database load balancers “split” the traffic your database receives between different servers lessening the load on your main database server, so that your database server can accept more traffic as necessary. MySQL and its counterparts are widely known for a ProxySQL database proxy appliance that runs as a MySQL daemon and allows organizations to make use of the full power of their MySQL database architecture.
- Update your applications frequently: application security and database security is closely related. By keeping all of your applications up to date, you increase your database security by tens or maybe hundreds of times.
- Audit your database security: last but not least, audit your database security frequently. Frequent database security audits will make sure that your database is in a great security posture and lessen your exposure to data breaches. For MySQL, there are plugins like MySQL Enterprise Audit that lets you audit the security posture of your database at all times. Other database management systems may have similar appliances — to further your database security, do your research and select the appliance of interest to you.
Follow the aforementioned database security tips to better secure your database and the data within. As sad as it may be to state though, there is no such thing as 100% security — and that’s why you should consider making use of data breach search engines like BreachDirectory. The data breach search engine built by BreachDirectory will let you assess the likelihood of your identity being stolen in a data breach and if the data breach search engine finds that the likelihood of you falling victim to identity theft is rather high, it will provide you with tips on how to protect yourself and your most precious assets within the data realm.
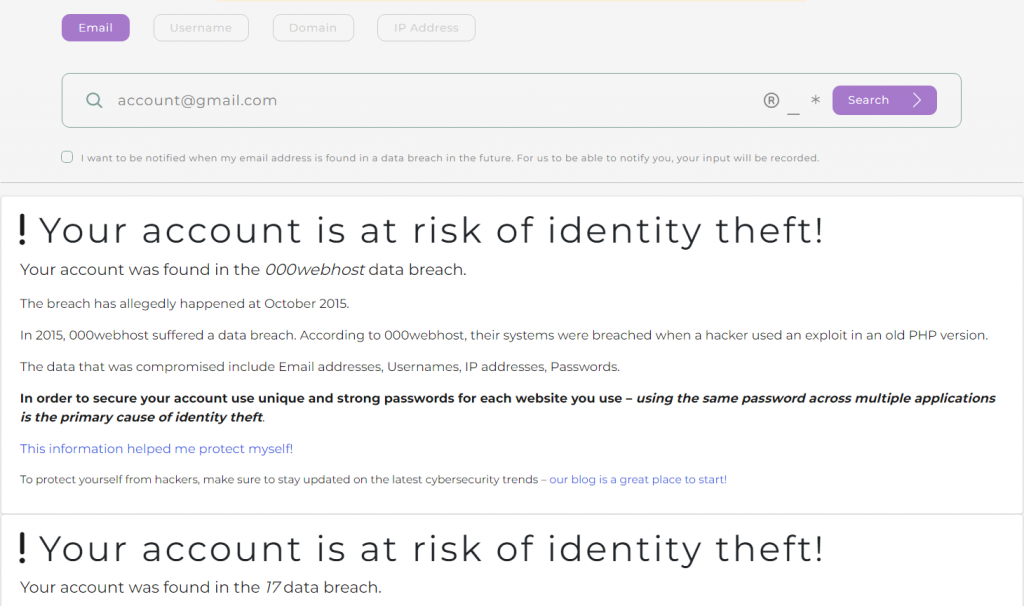
The BreachDirectory API will help you protect your clients and everyone around you, too — the BreachDirectory API will let you derive data from the data breach search engine in a JSON-based format and implement the data into your application or system for your use case. To further your database security, start using the BreachDirectory API today, and until next time.
Summary
In the wake of recent data breaches, takedowns and other nasty things in the cyberspace, it’s crucial to improve our database security posture. Our database security posture can and should be improved by using strong passwords, taking application and database server security into account, making sure all of our applications are kept up to date, backing up data frequently, and auditing the posture of our databases as well.
We hope that this blog has been useful for you, don’t forget to follow us on X (Twitter), LinkedIn, and Facebook for more updates, and until next time.
FAQ
How to Improve Database Security?
To improve database security, make use of the ten database security tips outlined in this article. Back up your data frequently, make sure to use strong passwords, and take application security into account. Don’t forget about the security of your online accounts either!
How to Improve Application Security?
To improve the security of your applications, make sure to follow code security best practices, adhere to the tips within the OWASP Top 10, and follow cybersecurity blogs like BreachDirectory to stay on top of the news in the cyber space.
Why Should I Use Data Breach Search Engines Like BreachDirectory?
Consider using data breach search engines like BreachDirectory to further database security because such data breach search engines allow you to check whether any of your online accounts are at risk of identity theft. If they are, BreachDirectory will provide you with valuable tips and feedback on how to deal with such issues.